originally published in Lawyers Weekly “Potential hotbeds of anarchy.” That’s how Stewart Mader initially described certain public wikis. As an author, consultant and founder of Grow Your Wiki, Mader helps businesses implement this still-fresh Web 2.0 technology, but he admits that negative publicity surrounding select public wikis
Read more →originally published in Lawyers Weekly David Woolford, a partner with Cassels Brock & BlackWell LLP, may conduct business from home (an hour commute from the office), the cottage (even farther) and locales like Germany or Hawaii. Kevin Davidson, a general civil practice attorney “based” in Appleton, Wisconsin,
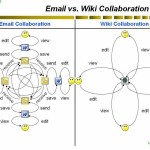
Read more →Originally published in National Magazine Good lawyers have always been good collaborators. Have we entered an age where the most technologically tuned online collaborators win the lion’s share of business? Perhaps. Many of today’s web-based software arrivistes enable lawyers to handle more of their business online than
Read more →Originally published on CBA PracticeLink. U.S. border security policy poses a potential threat to solicitor-client privilege. Here’s what you need to know, and how you can protect sensitive data.
Read more →originally published in The Lawyers Weekly “I have been practising on my own since 2002 and slowly filling up a wall of shelving with bankers’ boxes of files,” said Colorado Springs, CO-based attorney Tomasz Stasiuk. “When it came time to start another wall of boxes, that started
Read more →Brand consistency just one aspect of the issue originally published in itbusiness.ca It drives marketers crazy when a salesperson or channel partner takes something done by Marketing, changes it and creates their own content, says Bryan Bogensberger. That’s the tip of a massive iceberg currently hobbling many
Read more →originally published in The Lawyers Weekly The definition of futility: penning a review for Adobe Acrobat in a legal publication. Acrobat has pervaded the legal profession to the point that whether to acquire it is no longer at issue. But it isn’t futile to ask whether to
Read more →Originally published in Allstream Mindshift It has the makings of a perfect storm Today’s hackers are putting ego behind them as they use the promise of profit to drive their illicit Net activity. New regulations and industry practices mandate full dis-closure whenever personal or sensitive information is
Read more →Originally published on itbusiness.ca In August, IBM spent $1.3 billion to buy Atlanta-based Internet Security Systems Inc. (ISS). Analysts and ISS customers alike laud IBM’s acquisition In particular of the ISS managed security services portfolio. Managed security services providers (MSSPs) serve firms that choose to outsource some
Read more →